An in-depth look into authentication factors, use cases and best practices for securing IT infrastructures and protecting them from data breaches
by Ajay Kumar, Information Technology Security
 It is becoming increasingly obvious that security programs that are reliant on single-factor password-based authentication systems are doomed to fail. As Verizon noted in its 2013 Data Breach Investigations Report, the use of something other than a single-factor username-password credential would have likely thwarted 80% of the hacking attacks reported last year. Yet many enterprises still don’t use multifactor authentication.
It is becoming increasingly obvious that security programs that are reliant on single-factor password-based authentication systems are doomed to fail. As Verizon noted in its 2013 Data Breach Investigations Report, the use of something other than a single-factor username-password credential would have likely thwarted 80% of the hacking attacks reported last year. Yet many enterprises still don’t use multifactor authentication.
With that in mind, here is a look at two-factor authentication — options offered by technology providers and how to make a strong business case for enterprises to implement it as part of a comprehensive enterprise security strategy.
While many vendors have similar technology, they all come with their own pros and cons. For examples, the vendor with mature offerings may have proprietary authentication methods and a software development kit (SDK) that allows it to plug into enterprise applications or vendor applications. Others may focus on one or a few well known authentication methods such as one-time password (OTP) tokens and out-of-band (OOB) authentication methods.
Two-factor authentication
Enterprise IT systems provide specific capabilities to specific users; for example, the tasks performed by a system administrator differ from those a security analyst or financial analyst performs. Authentication is a critical business process that connects users to applications and other resources without exposing data and processes to which users are not authorized.
In today’s complex and cloud computing age, enterprises can adopt a two-factor authentication option to support one or more use cases to better protect enterprise assets and business data against unauthorized access. Those use cases include the following:
- internal or local access: employee access to critical business or cloud-based applications, and/or administrator access to corporate servers and network devices;
- external or remote access: remote or mobile employee access to the corporate backend systems via the VPN or portal access
- common network entry points: Between the public network/Internet and the internal corporate network, facilitating secure access to enterprise services like email or the VPN.
 Two-factor authentication as a technology has matured in recent years and technology costs have gone down significantly. While there have been evolutions and enhancements in the technology, now employees no longer need to always carry a cumbersome token device with them. A simple mobile device carried by every employee today can be used as a second authentication factor to deliver the secure authentication code instead of a token to protect the enterprise assets from hackers or attackers.
Two-factor authentication as a technology has matured in recent years and technology costs have gone down significantly. While there have been evolutions and enhancements in the technology, now employees no longer need to always carry a cumbersome token device with them. A simple mobile device carried by every employee today can be used as a second authentication factor to deliver the secure authentication code instead of a token to protect the enterprise assets from hackers or attackers.
Some major two-factor authentication vendors are Entrust, RSA, SafeNet and Symantec; all offer established, broad technology options and a range of viable use cases for enterprises.
RSA, the security division of EMC, has its secureID one-time password hardware and software-based tokens. In addition, it offers adaptive authentication, which is used by large enterprises to take the advantage of contextual authentication/adaptive access control capabilities. Identify verification, another option, is a managed service that offers identity proofing with validation based on end-users’ life-history questions and uses interactive user authentication processes. Most of its competitors sell similar products.
Sensitive data
The implementation pricing of 2FA basically depends on the scenarios. For example, the industry verticals, and the size of the enterprise, the usage pattern, user geography, helpdesk presence and sensitivity of the business or data and would cost between approximately $65,000 and $2 million for big financial and retail banking verticals.
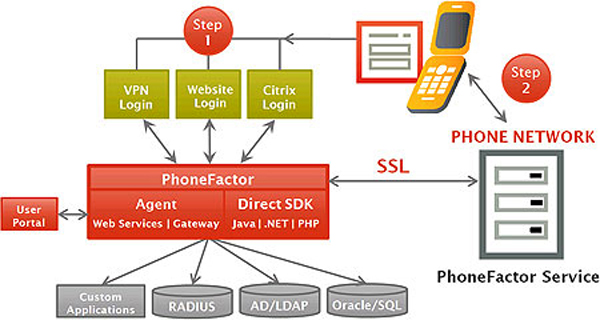
An example of a newer but established type of 2FA is the one offered by PhoneFactor (now owned by Microsoft). PhoneFactor leverages the user’s existing phone in lieu of a token or other dedicated 2FA device, it is convenient for users and is a cost-effective, secure platform for enterprises. During the first step of the authentication process, the user must enter his user name and password. In the second step, the user can choose one from among these methods: a) PhoneFactor calls the user and user simply answers by pressing # on the phone keypad, b) PhoneFactor sends out a text message containing the passcode and then the user replies to the text message with the passcode, c) PhoneFactor pushes a notification to the PhoneFactor app on the user’s smartphone and the user just taps “authenticate” in the app to complete the authentication process. For small organizations (up to 25 users), the vendor offers a free version.
User credentials
Two-factor authentication technology helps enterprises protect user credentials and reduces the number of incidents related to unauthorized access and theft of credentials in the corporate environment. In addition, it brings the enterprise in compliance with the regularity standards and meets the compliance requirements. For example, PCI DSS 8.3 reads, ‘Incorporate two-factor authentication for remote access to the network by employees, administrators and third parties’.
Compliance
Not all enterprises must be PCI compliant, but the PCI DSS is considered a baseline set of requirements, so organizations that don’t already have a 2FA strategy in place would be wise to begin the process, which of course includes evaluating vendor technology.
Organizations should consider the recommendations listed here while identifying their 2FA needs and plan the project accordingly.
- understand the corporate IT environment — This could include understanding the technologies landscape that’s used inside or outside the enterprise to access information or data and knowing how the IT policies are enforced and what protections are in place. For example, are the employees allowed to access corporate information through mobile devices? Or is the enterprise using SaaS applications hosted by SaaS providers, and do the SaaS providers support the 2FA security measures to protect the data;
- find the target users — Is 2FA considered only for selected business units like sales or marketing departments or for remote works and partners as well? In general, most organizations only offer 2FA for VPN access. Limit the implementation, at least in the early stages, to specific use cases;
- adopt a risk-based approach — Most organizations today implement a technology if it will help reduce risk. So alternatively when there isn’t a clear scope or group of target users, offer 2FA only to users who access business critical information or intellectual property, whether the user is an employee or third party and is accessing the information from within the corporate network or from a remote location.
- avoid unnecessary cost and complexity
The overall cost of the implementation can vary vendor to vendor depending on the size and requirements of the enterprise. Take into account the number of users, office locations, the global presence of the enterprise, plus support and help desk coverage factors when determining the cost.
Implementation
Two-factor authentication is not easy to implement. For instance, security firm Duo Security recently reported a serious flaw in Google’s two-step login process. The problem, which was soon fixed, stemmed from Google applying the feature across its many services. Despite being one of the Internet’s giants, while its technology was solid, its implementation was flawed.
To be clear, such a broad undertaking like 2FA is bound to have complications in any organization. But the lesson is that while implementing a single, secure infrastructure-wide two-factor authentication platform is not without stumbling blocks, being aware of likely problems before you begin can help lessen the effects.
For example, legacy software and services must often be reworked to handle 2FA or may require an authentication framework that could be used among different in-house or outsourced tools to support the two-factor authentication enterprise-wide. Sometimes it becomes clear that the two-factor authentication framework selected simply requires too much customization, something that can be difficult to determine until software architects actually get to work on integration aspects of the implementation.
Two-factor authentication will likely be seen by users as a hassle. They may find it tedious to have a trusted device or hardware token with them at all times in order to log in. So some authentication scenarios may require an option for users to skip two-factor authentication for frequently accessed systems. These and other pain points of a two-factor authentication implementation may be eased with the following measures:
- select a factor that fits enterprise needs. The options include hardware-/software-based tokens or sending SMS messages to smartphones. Enterprises that are geographically centralized will appreciate physical tokens, while others with a constantly moving workforce may wish to use software-based tokens or mobile options;
- consider implementing a phased approach. Abrupt, enterprise-wide cutovers don’t make anyone happy. At the same time, application and system owners will find it easier to migrate everyone at a single go. But that just creates a nightmare for end users and help desk staff members who have to support and address the issues that occur during the migration. It could shoot up the project cost too;
- provide sufficient user support. Getting the back-end server components installed and configured takes a while, and integrating and testing applications takes time too. Self-service, sufficient training and a well-staffed helpdesk and support team will be essential to get users accustomed to the technology and able to successfully navigate through the transition period.
Modern enterprise
Two-factor authentication is becoming an essential element of modern enterprise IT security programs, yet it remains complex and difficult to understand, implement and manage. Organizations must understand that traditional and inherently weak password-only authentication mechanisms may no longer serve as an adequate security control. Furthermore, amid today’s threat landscape, it’s apparent that two-factor authentication is necessary in order to keep unauthorized users from obtaining access into key corporate systems and keeps persistent, sophisticated attackers at bay.